
Malcom Gladwell, Arianna Huffington to headline VOICES Virtual. Register for Free

Our best-in-class infrastructure protects customer data throughout its entire lifecycle in the platform. A powerful suite of customizable settings and tools also afford our customers the autonomy to further define their own security and privacy parameters.
We strongly believe that security shouldn’t be a second thought. With Staffbase’s enterprise-ready support, all of our customers can fully depend on a safe and reliable platform suited to their needs and concerns.
As of March 2023

All Staffbase certifications and compliance documents are available at Staffbase Trust Center.

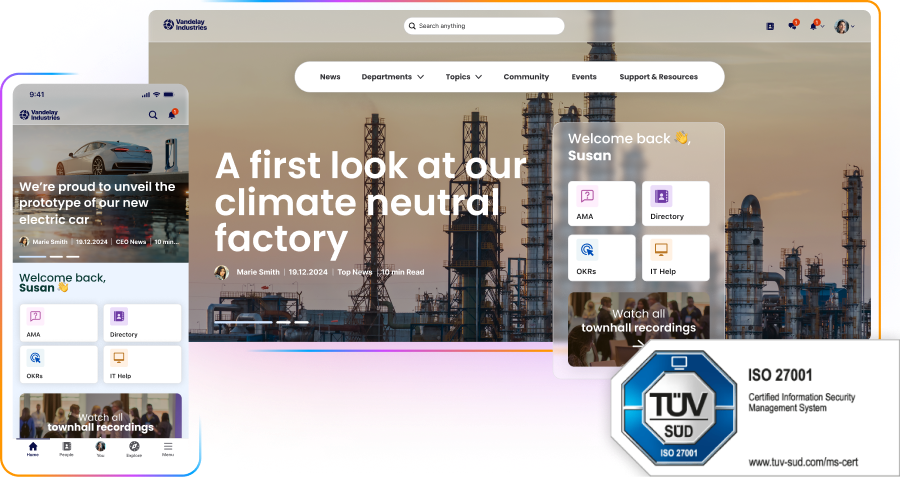
Over 2000 businesses and over one million of their employees around the globe rely on the Staffbase platform and products every day to securely communicate within their company. Our customers have a wide variety of security and privacy needs, with many coming from the most highly regulated and security-sensitive industries in the world. With this in mind, security is of utmost importance to our platform and vision.
At Staffbase, our strong foundation of product features and provider processes ensures industry-leading protection across the board.
We understand that hosting locations are important for our customers and their compliance requirements. As a result, Staffbase customers can choose between EU hosting or US hosting for the services. More information on our providers can be found at our subprocessor page .
External hackers are also welcome to submit findings with CVSS ratings >= 9.0 through our public page here and automatically get invited to our private bug bounty program at hackerone.com.

With its roots in Germany and the EU, Staffbase has put privacy and data protection at the core of how we have developed our products, services, and our internal governance. Germany has some of the strictest data privacy laws in the world, and we bring our experience in Germany into the way we develop and build employee communications.